Ethereum didn’t “choose” to feel slower or more expensive at times. It chose a philosophy, and the blockchain trilemma explains that philosophy in one sentence.
If you’re building, investing, or picking an ecosystem to commit to, the trilemma is one of the fastest ways to predict a network’s next moves. It tells you what a chain will sacrifice by design when pressure hits: will it preserve decentralisation even if fees spike, push scale even if validator power concentrates, or harden security even if throughput stays constrained?
Once you understand the trilemma, you can read roadmaps like you read incentives. Ethereum’s rollup-centric strategy, Solana’s performance-first engineering, and modular stacks that separate execution from data availability all make more sense when you view them as trilemma trade-offs, not marketing narratives.
The Three Corners of the Trilemma
The trilemma only becomes useful when each “corner” is defined in operational terms.
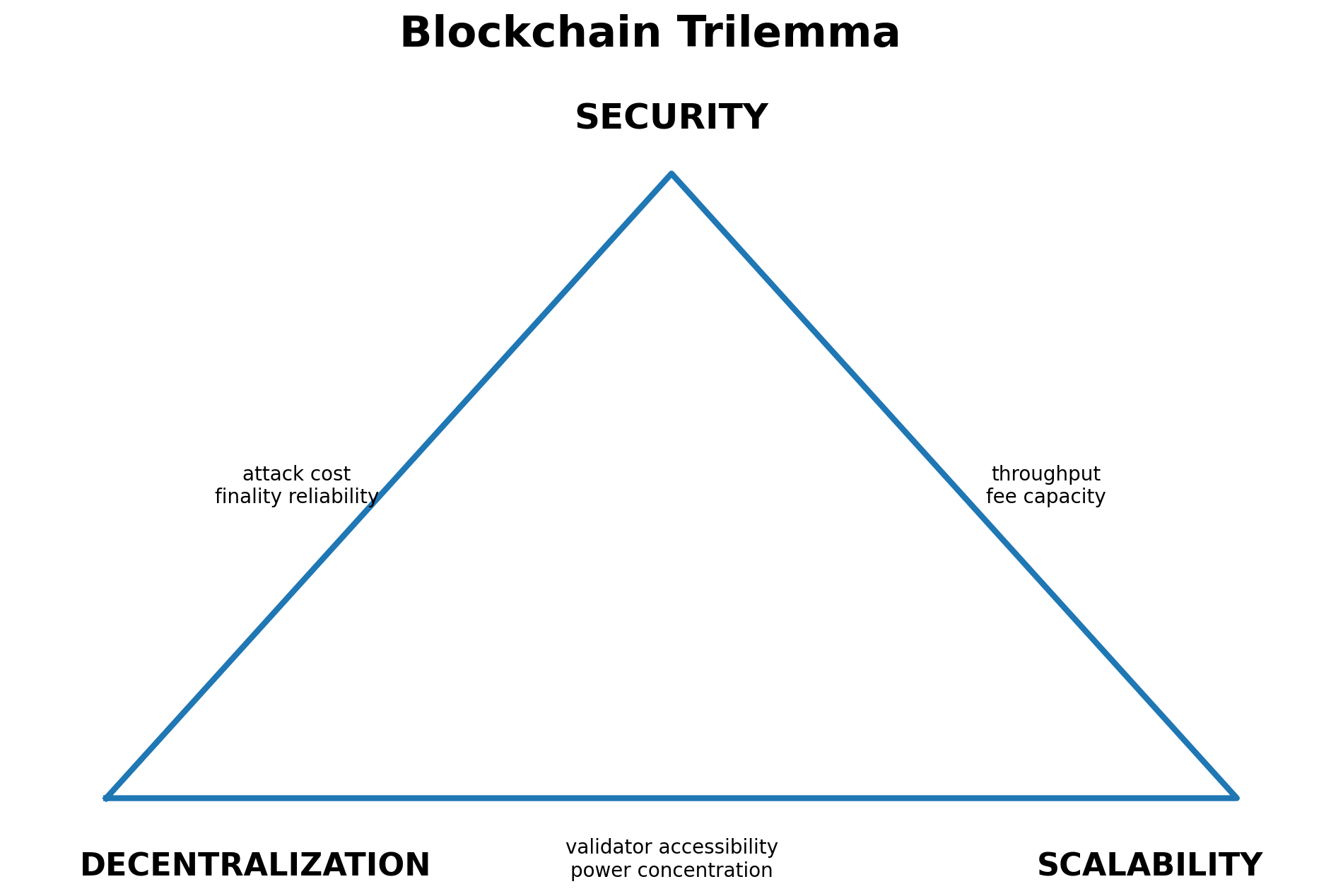
These are three practical goals every blockchain wants at the same time: strong security (hard to hack or rewrite), real decentralization (no single company or small group controls it), and scalability (fast and cheap enough for lots of people to use).
The blockchain trilemma is the problem that it’s difficult to maximize all three at once when a network pushes hard on one corner, it usually weakens at least one of the other two.
That’s why claims of “solving the trilemma” usually mean the trade-off got shifted somewhere else, such as higher hardware requirements that reduce validator participation, more concentrated governance, or extra trust assumptions introduced through scaling layers or operational shortcuts.
1. Decentralization
Decentralization ensures that no single entity or small group “runs the network.” It relies on a vast, diverse array of independent validators to verify transactions and maintain consensus.
The Decentralization Tension
The trilemma dictates that as decentralization increases, maintaining scalability and security becomes significantly more complex:
- Decentralization vs. Scalability: To keep participation open, a network must maintain low barrier-to-entry costs (modest hardware and bandwidth). However, scaling requires processing more data at higher speeds. These high resource demands price out smaller validators, concentrating power among elite operators with high-performance setups.
- Decentralization vs. Security: If a network scales while attempting to remain decentralized through “shortcuts”—such as reduced validator counts, faster block times with less verification, or heavy reliance on off-chain components—it introduces new security vulnerabilities. With fewer independent parties truly auditing the system, the cost of an attack drops.
The Balancing Act
Networks face a constant trade-off:
- Low Requirements: Keeping hardware needs light protects decentralization but often caps throughput, limiting the network’s ability to scale.
- High Requirements: Prioritizing speed through “industrial-grade” infrastructure enables scalability but forces control into the hands of a few, eroding the very essence of a decentralized protocol.
2. Security
Security defines a network’s resistance to attacks—specifically its ability to prevent transaction reversals, history rewrites (reorgs), double-spending, and censorship. High security is achieved through robust economic incentives, a vast network of independent validators, and battle-tested software.
The Security Tension
In the trilemma, maximizing security often stifles scalability or decentralization:
- Security vs. Scalability: High security requires redundant, independent verification by many nodes. This rigorous “double-checking” increases latency and caps throughput. Conversely, reducing validation to gain speed makes the network cheaper to attack.
- Security vs. Decentralization: Increasing performance while maintaining security often requires powerful, expensive hardware. This high barrier to entry concentrates control among a few wealthy operators, weakening decentralization.
The Business Trade-off
This creates a critical crossroads:
- Low Security: Institutions view the chain as “demo-grade” and unsafe for high-value settlement.
- Over-Prioritized Security: The network becomes too slow and expensive for mainstream adoption.
3. Scalability
Scalability is the network’s capacity to handle growth—more users, more transactions, and more complex applications—without a corresponding surge in costs or a decline in performance. It is the “engine room” of the trilemma; while security and decentralization provide the foundation, scalability determines a network’s commercial viability.
The Scalability Tension
To scale, a network must process more data faster. However, traditional “Vertical Scaling” (improving a single chain’s performance) creates immediate pressure on the other two pillars:
- Scalability vs. Decentralization: Increasing throughput often involves larger blocks or faster block times. This requires nodes to have massive bandwidth and expensive, high-end hardware to stay in sync. When only a few “industrial-grade” data centers can afford to run nodes, the network becomes centralized.
- Scalability vs. Security: Some chains gain speed by reducing the number of validators or “skipping” certain verification steps. This makes the network faster but lowers the cost for an attacker to compromise the system, as there are fewer independent parties checking for fraud.
The Impact on Unit Economics
Scalability is not just a technical metric; it is a business constraint.
- Congestion Pricing: When demand exceeds a chain’s capacity, “Gas” or transaction fees spike. This “surge pricing” prices out mainstream users and makes micro-transactions (like gaming or small payments) impossible.
- Latency: Low scalability leads to high latency (long wait times for confirmations). In a competitive market, a delay of even a few seconds can make a platform feel “broken” compared to centralized alternatives like Visa.
Why the Trilemma Keeps Reappearing
The trilemma shows up because blockchains do two hard things at once: they coordinate many independent operators and they assume some of those operators may be adversarial.
As you increase the number of parties that can validate (decentralization) and strengthen the system against attacks and failures (security), you also increase the amount of communication, verification, and coordination the network must do before it can confidently finalize transactions. That coordination overhead is the core friction that repeatedly constrains throughput and latency (scalability).
It explains why some networks stay slower but feel safer for high-value settlement, why others feel fast but carry higher trust or attack assumptions, and why teams like Ethereum push scaling to Layer 2 rollups instead of forcing the base layer to process everything.
Most public chains therefore converge on a small set of trade-off patterns:
- Scale the base layer aggressively → decentralization pressure – When a chain targets very high throughput on L1, it often raises validator requirements (hardware, bandwidth, storage) or concentrates validation into fewer professional operators. That can improve performance, but it narrows who can realistically run a validator and increases the risk that a smaller set of entities can coordinate, censor, or influence governance.
- Keep validation widely accessible → scalability limits – If a chain prioritises low barriers to validation—so more people can run nodes and verify independently—it typically keeps blocks smaller, execution simpler, and consensus more conservative. That improves resilience and credibility, but it limits how much activity the base layer can process without raising centralisation risk.
- Scale “around” the base layer (Layer 2 or modular designs) → complexity moves to the edges – Rollups, app-specific chains, and modular stacks can expand capacity without forcing L1 to become heavy. The trade-off is operational: interoperability, bridging risk, sequencer design, data availability assumptions, and user experience become part of the security model. You often gain scalability, but you now manage a system-of-systems where failure modes shift from L1 consensus to cross-layer coordination and governance.
How Modern Blockchains Manage the Trilemma
Modern networks rarely “solve” the trilemma outright. Instead, they redesign where the trade-offs sit. Each approach can increase throughput, but it also introduces new dependencies (sequencers, bridges, data availability assumptions, governance controls) that must be treated as part of the system’s real security model.
1. Layer 2 rollups (scale without changing the base layer’s security model)
Ethereum’s roadmap puts significant scaling weight on Layer 2 rollups—systems that execute transactions off-chain (or off the base layer), then post data/proofs back to the base chain. The key idea: L2s can inherit the base layer’s security while delivering lower fees and higher throughput, as long as the rollup design and data availability assumptions hold.
What this trades off: less “one-chain simplicity,” more reliance on rollup operators/sequencers, bridges, and cross-domain UX.
2. Sharding / data scaling (scale the data layer, not just execution)
Another approach scales by increasing the amount of data the network can carry, which supports rollups and other execution layers that need data availability to remain secure. Ethereum positions this as part of its scaling approach alongside rollups.
What this trades off: more complex protocol design, longer upgrade cycles, and greater engineering surface area.
3. High-performance L1 design (scale the base layer directly)
Some chains prioritise throughput and low fees by tightening validator requirements or reducing the cost of consensus coordination.
What this trades off: decentralisation can weaken if only a smaller set of validators can realistically keep up, or if infrastructure centralises around a few operators.
Applying the Trilemma in Real Decisions
The blockchain trilemma is a tool for auditing risk. Every network “solves” it by shifting constraints—usually by trading validator accessibility for speed or security for convenience.
Strategic Trade-offs
- Settlement & Treasury: Prioritize Security and Finality. These flows require a conservative base layer where transactions are immutable, even if fees are higher.
- Consumer Apps: Prioritize Scalability. These require Layer 2 (L2) rollups to ensure a seamless UX, but must account for “operational plumbing” risks like sequencer downtime.
- Institutional Products: Prioritize Governance and Compliance. This adds a layer of policy controls and audit trails to ensure operations remain defensible to regulators.
How to Use This to Your Advantage
Stop looking for the “fastest” chain. Instead, match the infrastructure to the asset value. 1. Use highly decentralized, secure layers (like Ethereum L1) for core settlement and large treasury holdings. 2. Use scalable layers (L2s) for high-frequency activity. 3. Bridge the gap with institutional-grade middleware that enforces your specific risk policies (who can move funds, where, and under what approval).
Secure Your Scale with ChainUp
Don’t gamble on operational fragility. ChainUp provides the infrastructure that turns the trilemma from a risk into a manageable operating model.
We empower your team with:
- Institutional-Grade Wallet Solutions: MPC and Multi-sig wallet architectures.
- Programmable Compliance: Role-based permissions, withdrawal allowlists, and automated approval workflows.
- Audit-Ready Operations: Real-time monitoring and provable control evidence for regulators.
Build on the right rails—Talk to a ChainUp Expert today.